Wireless keyboards are often used in office environments due to their convenience. Wireless keystrokes are transmitted by the keyboard to a wireless receiver that feeds the keystrokes to a computer. Earlier models of wireless keyboards transmitted keystrokes without applying any cryptography. This was a problem as attackers could be listening in
To address the problem manufacturers started to apply cryptography to ensure that only a specific wireless receiver would be able to receive keystrokes from a specific keyboard. Articles recently started to appear in the media that claim that it is possible to decrypt encrypted keystrokes generated by some keyboards and that it is even possible to generate encrypted keystrokes, thereby allowing an attacker to remotely control a computer.
Concerned parties have been contacting us to find out how severe the problem really is. We attempted to reproduce popular attacks on wireless keyboards. This article describes what we did as well as our findings.
The keyboard
We decided to use a Logitech K360 keyboard since the keyboard is widely used in
The Logitech K360 keyboard tested contained a C-U0007 Unifying USB dongle. Before we performed any testing we ensured that the latest firmware was loaded.
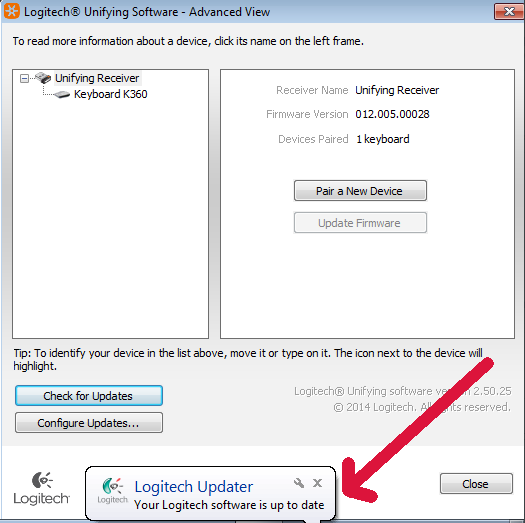
While researching the problem we also discovered an updater for Logitech Unify dongles available on the Logitech support site. We downloaded and applied the update.
What is interesting is that the firmware version displayed is different after applying the update. This is interesting as the Unifying software indicated that everything is up to date. Maybe the “Check for Updates” only checks the Windows software and not the firmware running on the Unifying dongle or keyboard (but this is only a guess). We did not explore this in any more detail.
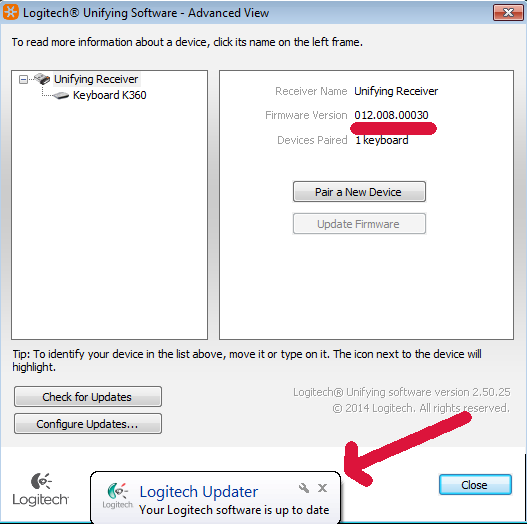
Unifying dongle firmware version. 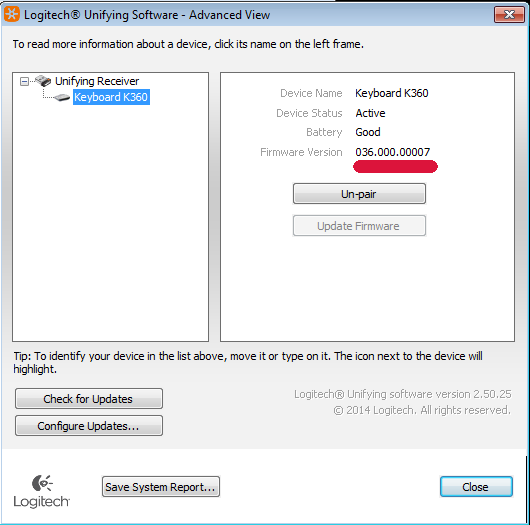
K360 Keyboard firmware version.
We updated the firmware on 10 August 2019. The test results discussed in this article have been reproduced using the (latest) firmware.
Bastille Research keysniffer
In 2016 Bastille R
It turns out that a firmware update has been issued for the K360 keyboard to address the issues identified by Bastille Research. This may explain why the results could not be reproduced.
LOGITacker
A few weeks ago Marcus Mengs revealed vulnerabilities in the Logitech Unifying system that allows attackers to read keystrokes transmitted by wireless keyboards and also to inject keystrokes.
We followed the instructions posted on the LOGITacker Github page using the Nordic Semiconductor nRF52840 USB development kit. We could successfully reproduce the results obtained by Marcus Mengs.
More specifically, we could do the following:
- Uncover the shared secret used by the keyboard and Unifying dongle for encryption. The shared secret could be captured when the pairing was performed, using the standard Unifying software, and when a re-pair was forced using a utility developed by Marcus Mengs to force the keyboard and Unifying dongle to pair.
- Decrypt the encrypted keystrokes transmitted by the keyboard, thereby revealing all the keystrokes pressed on the K360 keyboard.
- Inject encrypted keystrokes.
We could not do the following:
- It was not possible to read keystrokes transmitted by the keyboard without uncovering the shared secret used by the keyboard and Unifying dongle. The keystrokes are encrypted (for this keyboard and firmware version) and cannot be viewed without decrypting the keystrokes.
Demonstration
A short demonstration video was created to explain the problem and demonstrate the problem in action. We attempted to make this video as non-technical as possible to ensure that the video is understood by a wider audience.
Protecting yourself
The method used to uncover the shared secret used by the Unifying dongle and wireless keyboard was uncovered by intercepting the pairing process between the Unifying dongle and the keyboard.
An attacker has two options when attempting to exploit this vulnerability:
- Wait for owner of the keyboard and Unifying receiver to re-pair the devices.
- Force the keyboard and Unifying dongle to re-pair (demonstrated in the video).
The first option is not very practical (in many cases) as the attacker (and/or his/her equipment) will have to be close enough to capture pairing packets sent between the Unifying receiver and the wireless keyboard.
Since pairing is not performed often, attackers may attempt to force the Unifying dongle and keyboard to re-pair. However, to do this, physical access to the Unifying receiver (and keyboard) is required. Please be aware that a different attack exists where the shared secret can be read directly from the Unifying dongle. We have not tested that specific attack as the attack discussed in this article is severe enough to fully compromise the security of the keyboard.
Consider doing the following to protect yourself:
- Treat your Unifying dongle as you treat a flash disk – lock it away when you are not using it.
- Only pair your devices in trusted environments. Pair your devices at home – don’t pair your device in public places such as train station, bus stops and coffee shops.
- Consider the sensitivity of the work that you are doing on the keyboard. It would be wise to use your laptop keyboard or keyboard with a cable for sensitive work until a firmware update is released that addresses the issue.
- Update your device when new firmware is released.
Conclusion
The Logitech K360 keyboard was tested for security vulnerabilities. We could reproduce the LOGITacker experiments, thereby reading encrypted keystrokes and writing encrypted keystrokes. Please note that only the Logitech K360 keyboard was tested. The results that we obtained are valid for the keyboard that we tested. However, other keyboards may not necessarily produce the same results. Furthermore, other
It would be best to contact the keyboard manufacturer if you are unsure about the safety of your wireless keyboard.
Notes
During
- 3:21 – Dongle disconnected. Retried the same command.
- 3:28 – Actual command: inject target [address].