At Crimson Wall we recently performed an interesting malware experiment. We downloaded thousands of malware applications, ran them and documented their behaviour. The results obtained were in some cases not what we expected. The experiment and results obtained are discussed in more detail in this article. Some of the research findings were presented at the 2019 0xcon conference.
We are constantly warned about the dangers of malware. The quote below shows the view of a well-known company involved in the field of malware.
Ransomware is now one of the key cyber threats facing organizations and can have a major impact on their bottom line, from financial losses, disruption, and reputational damage. Attacks where dozens or even hundreds of computers are infected can leave businesses with enormous cumulative ransom demands. – Symantec, 2017.
Sophos, also a well-respected company involved in the field of malware, paints a similarly bleak picture about the dangers of malware and malicious activities.
In the last year, phishing attacks have seen a meteoric rise as attackers continue to refine tactics and share successful types of attacks. In particular, they’ve taken advantage of the malware-as-a-service offerings on the dark web in order to increase the efficiency and volume of attacks. In fact, 41% of organizations now report at least daily phishing attacks – Sophos, 2019.
Other forms of malware, such RATs are are also often used by 3rd parties to unsolicited access to remote systems. In many cases, phishing emails are accompanied with malware to either steal a password, enable remote access to a system, or load malware onto an unsuspecting victim’s system.
The key to controlling the behaviour of malware is to understand what malware applications are up to. Understanding this will help us understand the risks to ultimately put proper controls in place to guard against popular malware applications currently in circulation.
Experiment setup
The only sensible way to perform a malware experiment is to automate as much of the process as possible. The acquisition, execution and retrieval of results were fully automated for this experiment. This helped to ensure that the experiment could run uninterrupted 24/7.
All malware applications were executed in a virtual environment (running on a Dell PowerEdge server). The firewall, UAC and anti-virus were disabled to ensure that the malware applications have the ability to freely infect and update the system as required. All system modifications were meticulously monitored and collected for later analysis.
To obtain malware samples was surprisingly difficult. Simply performing a Google search for malware did not provide the intended results.
Fortunately a malware repository, named theZoo, is available on Github containing many malware samples. However, to properly perform this experiment thousands of malware samples were needed. We used the API provided by URLHaus to obtain a list of malware URLs. The API was queried from time-to-time and the applications (.exe files) were downloaded. The downloaded files were executed in the virtual environment and the results were stored for later analysis.
Results
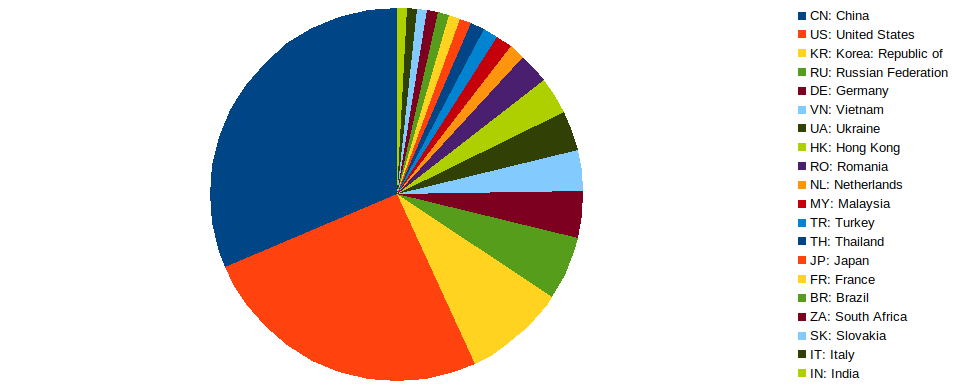
We downloaded a total of 11497 malware samples for this experiment. These samples were downloaded from websites all over the world. A total of 626 samples were downloaded from what is believed to be compromised WordPress sites. The figure below shows the most populous countries of origin for the malware samples downloaded.
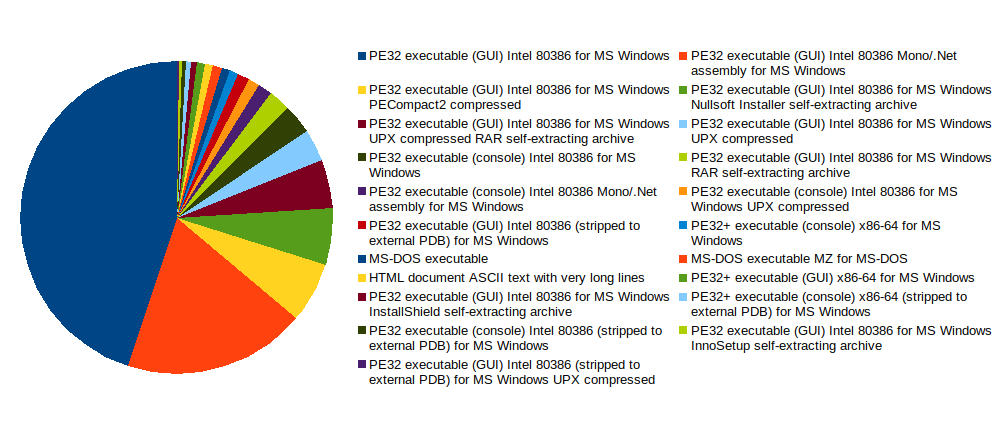
Various application types were downloaded, ranging from GUI-based Windows applications to DOS-based applications. The figure below shows the most popular formats of the downloaded malware applications.
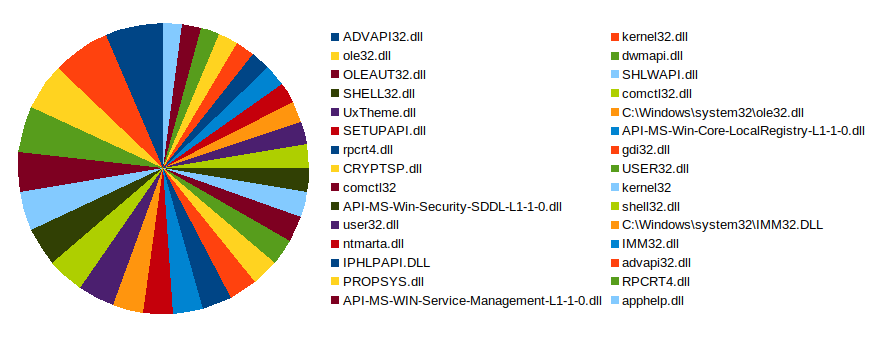
The most popular DLLs loaded by the malware applications were not very informative, as the most loaded DLLs are typically used by legitimate applications as well.
The most popular API call used is NTQuerySystemInformation, which can be used to retrieve interesting information about the system. Other interesting calls include WriteProcessMemory, ReadProcessMemory and LdrLoadDLL.
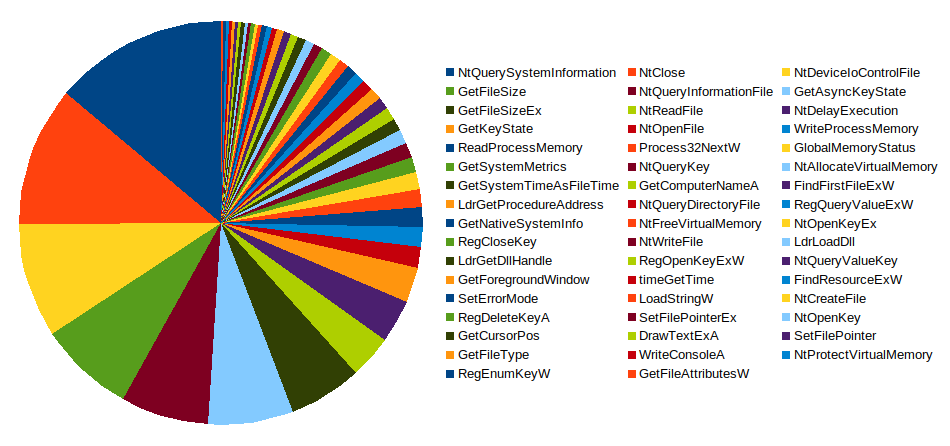
File and registry access attempts were also monitored but revealed little information specific to malware (as was the case for DLLs usage). However, monitoring failed file open attempts proved to be helpful. It turns out that some malware applications attempt to harvest application configuration files. Applications targeted include FileZilla, CuteFTP and many others.
All network requests generated by malware were monitored. Many DNS resolution requests were observed. Interestingly enough, 3139 requests were observed to domains that are obviously non-existent. A few examples of such domains are shown below.
| zxtlfcumlvxkrwsqsxthmvga.net |
| aybdhaqgvgxwvwibztxoljn.org |
| fqrwlfyprccqibtfnvuctdzh.info |
| jbgamfbeksnlvaebebqhidutcbusg.org |
| rcrqkaqptzhhxqglvsobuovei.biz |
| lhhlzaaebmfyxgmlgeytkzl.biz |
| zxgvcljylfqbobvocejeyxcnvx.com |
Malware applications typically submit DNS requests for non-existent domains to detect virus sandbox environments. Sandbox environments are often configured to intercept and manipulate DNS requests. This is typically done to redirect traffic to a resource controlled by researchers. The problem with this strategy is that manipulations can sometimes be detected.
An easy way to test for DNS manipulation is to submit a query to a domain that obviously does not exist. If a DNS result is returned with an IP address for a server, then it’s very likely that the malware is running in a sandbox environment or that some other form of manipulation is taking place. The presence of any manipulation usually stops malware from doing what it is supposed to do, thereby ensuring that malware researchers have a much harder time studying the behaviour of such malware.
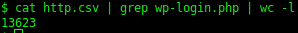
All HTTP requests were monitored. In total 34524 HTTP requests were observed.
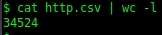
A total of 13623 of these requests were made to random WordPress login pages across the internet. This indicates that many malware applications may have been used to perform password spraying.
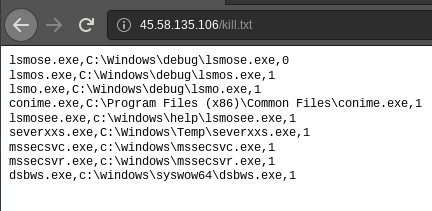
Recurring HTTP file downloads were also observed. References to files called “down.html”, “vers.html”, “kill.txt” were frequently observed. The list below shows files that were frequently downloaded by malware running in the virtual environment.
| http://45.58.135.106/ok/down.html |
| http://45.58.135.106/xpdown.dat |
| http://45.58.135.106/vers1.txt |
| http://45.58.135.106/ok/vers.html |
| http://45.58.135.106/down.txt |
| http://45.58.135.106/ok/64.html |
| http://198.148.90.34/64.rar |
| http://185.112.156.92/down.exe |
| http://45.58.135.106/kill.txt |
| http://174.128.249.18/item.rar |
The “kill.txt” file seems to contain instructions of applications to close, as shown below.
The file “down.txt” seems to contain instructions for files to download and the locations where the downloads are stored.
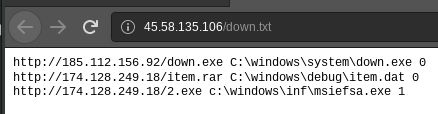
References to various dynamic DNS entries were observed. The table below shows a few of the names observed.
| bloc2020.ddns.net |
| manmannet.servep2p.com |
| iammrjeff00.duckdns.org |
| santzo.warzonedns.com |
| theeraser94.ddns.net |
| mandada.ddns.net |
| hugus.mywire.org |
| aliprince0422.duckdns.org |
| kartelicemoney.duckdns.org |
Some of the malware applications executed various commands from the command-line. A total of 3636 command-line executions were observed. The most popular application was reg.exe (the Windows registry editor) with 753 executions. Chrome was executed 157 times, Powershell 80 times and BITSadmin 108 times. The BITSadmin tool was used by malware applications to download Tor clients. Malware may therefore be responsible for unexplained Tor traffic on a network.
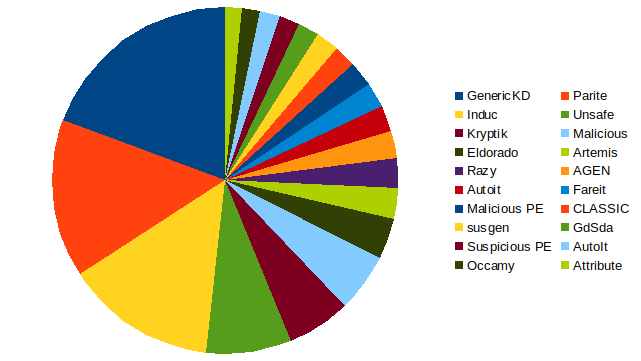
All malware applications were submitted to Virustotal. Virustotal allows various anti-virus systems to classify a piece of malware. The virus identification information returned by Virustotal most frequently is shown below.
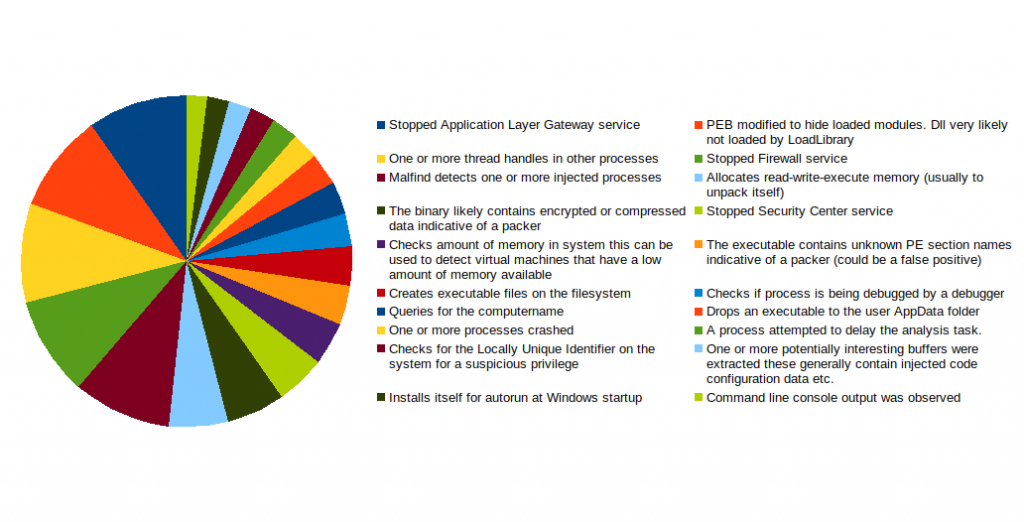
The behaviour observed most frequently during the execution of malware is shown below.
Lessons
- Ensure that your UAC, firewall and anti-virus are always enabled.
- Admin accounts should only be used to perform administration tasks (and not to perform day-to-day operations).
- If you do not want to purchase an anti-virus, at least turn on Windows Defender – tests performed by av-test.org recently indicated that Windows Defender is an excellent anti-virus solution.
- DNS queries to random domain names may indicate the presence of malware on your network.
- Frequent failed login attempts to random WordPress sites may indicate the presence of password spraying malware on one or more devices on your network.
- Unexplained Tor traffic may also indicate the presence of malware on your network.