In 1969 the groundbreaking RFC 15 was published describing a protocol known as Telnet. Telnet was used for many years to remotely log into systems. One of the amazing things about Telnet is its simplicity – it’s easy to understand and use, and if you are a developer, easy to implement as well. Telnet was definitely a groundbreaking protocol (for its time).
About 50 years have passed since RFC 15 was published. One key weakness of Telnet is its lack of security features. As a result, SSH has gradually replaced Telnet.
A few days ago a database containing thousands of usernames and passwords for network devices has been released. This database was reported to contain credentials for more than 515,000 devices.
The Crimson Wall team obtained the dump for further analysis. The entire database was available as a zip file (roughly 3MB when compressed). A word count on all files contained within the zip archive revealed that all text files in the archive collectively contained 516,716 lines.
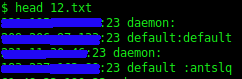
The text files in the archive basically contain the IP:port and username:password combinations of various devices on the internet.
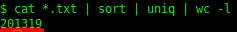
The text files were observed to contain duplicate entries. After filtering out all duplicate entries a total of 201319 unique lines remained.
It’s important to realise that the number of lines counted are not equal to the number of compromised devices. A more accurate estimate can be obtained by extracting all IP addresses (without including the port number) and then counting the unique IP addresses, as shown below.
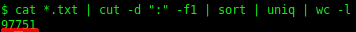
Roughly 97,751 unique devices were therefore listed in the breach. The most popular port listed in the database is port 23 (Telnet). The results produced included some noise (as shown below). Although only a few invalid entries were observed, it is important to note that the exact number of 97,751 did not take noisy data (as shown below) into account. The exact number of compromised devices may, as a result, be slightly different.
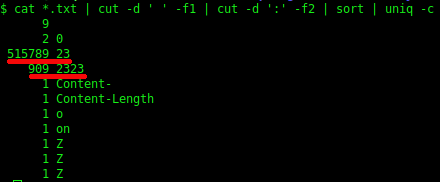
The most popular usernames are “root”, “default”, “admin” and “daemon”.
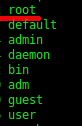
The most popular passwords appear to be blank (“”), “admin” and “root”. Some of the passwords below seem to resemble random strings. It turns out that some of these passwords are actually the root passwords used by a specific IP camera brand.
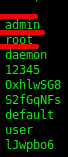
It is therefore plausible that many of the devices in the database may be IP cameras. All IPs in the database were passed to geoiplookup to identify the location of the devices. Most of the devices are located in China.
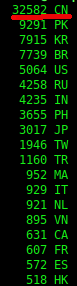
South Africa hosts 103 devices listed in the database.
It’s interesting to see that Telnet is still being used today. It’s also interesting to see that passwords such as “root” and “admin” are in use. What is concerning is that at the time of writing some of the devices listed in the database may already have been repurposed as slaves in a botnet or some other form of malicious activity.
Many owners of these devices are likely to be blissfully unaware of what is currently happening to their devices. This article contains a few lessons that may save your devices from ending up on a similar list:
- Your devices should not be exposing the Telnet port (23). Firewall Telnet or disable it completely.
- Do not assign public IPs to embedded devices (such as IP cameras) without having the proper controls in place.
- If you need to access your IP camera from the internet, simply place your camera on your LAN and use a VPN to securely access your camera from anywhere in the world. If this cannot be done, refer to bullet#1 and bullet#2.