In modern times phishing is a harsh reality. Phishing has come a long way from the simplistic Nigerian Prince type scams that once filled up our inboxes. Phishing has grown tremendously in sophistication. Investigating these phishing attacks is time-consuming, and it is often challenging to stop these phishing campaigns.
As the frequency and precision of phishing attacks seem to increase one can not help wondering how effective these attacks are and how many people are fooled into opening the gates to the mostly anonymous enemies.
In this article, we’ll have a look at the details surrounding a recent phishing campaign that was
Typically phishing investigations are part of the job and only rarely do events occur that are note-worthy. This specific investigation case is noteworthy because the database of users tricked into giving up their account details was uncovered. The database indicates that victims in this particular case were wise enough to see the phishing scan for what it was. As a result, the phishers were not extremely successful. Although this campaign was unsuccessful, and is not representative of the success rate of all phishing campaigns running daily, it is at least one success story that is worthy of sharing.
The campaign
An email was recently circulated to corporate email users around the world, informing them that they received encrypted messages. We have seen many of these messages. The typical message looks like the one below (the identity of the recipient has been masked):
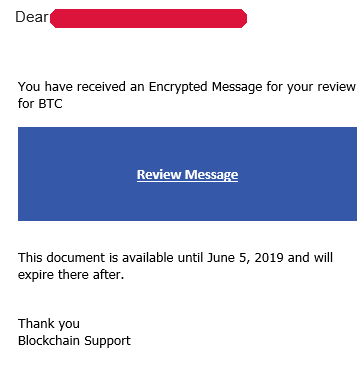
The email contained one link: https://blockchaincomexplorer.z13.web.core.windows.net
On the left is the phishing login screen and on the right is a screenshot of the login screen that is being impersonated.
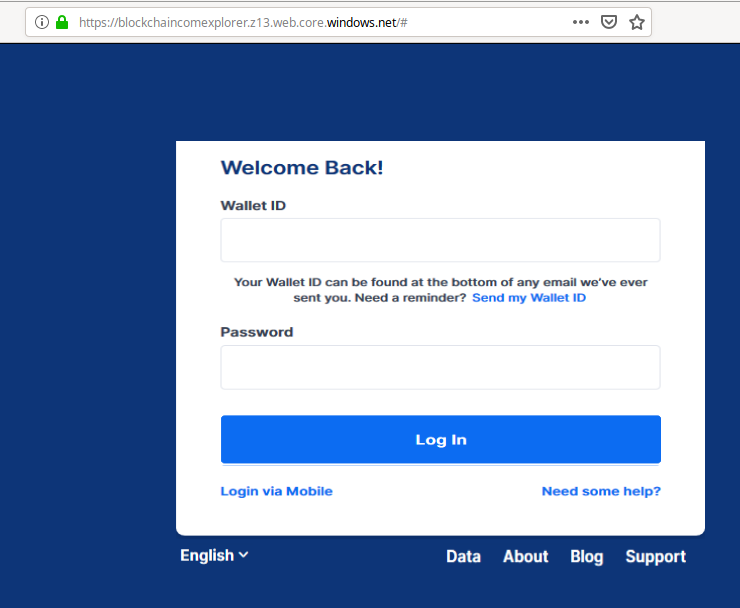
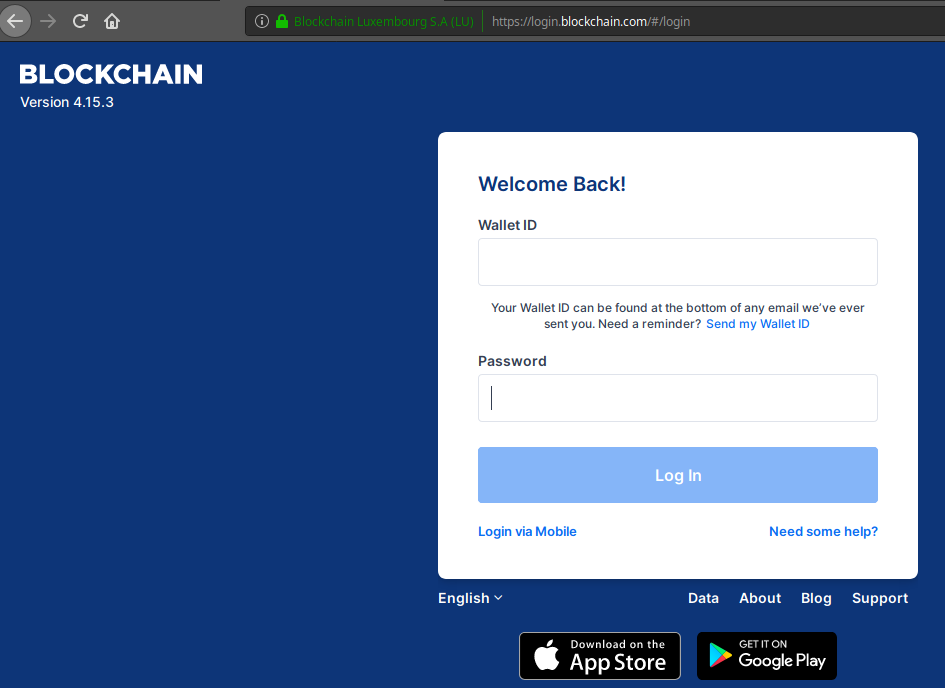
What is interesting is that the phishing login screen seems to be a screen grab of the original login page – the links do not seem to work. Only the Wallet ID, Password and “Log In” controls work.
Something even more interesting is that the phishing site seems to have a valid SSL certificate, issued by the Microsoft Corporation. At this point, everyone that was paying attention would now be asking if Microsoft has been hacked.
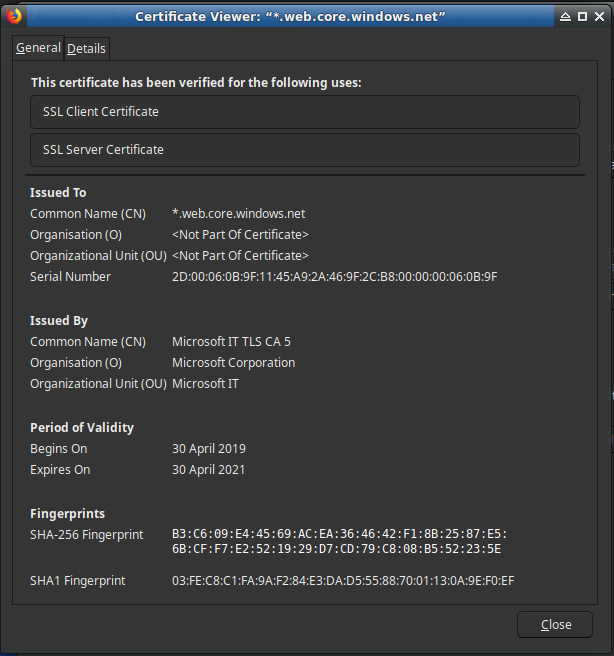
The answer is no – It turns out that Azure Blob storage is the latest technology to be used by phishers (as explained here: https://www.bleepingcomputer.com/news/security/outlook-and-microsoft-account-phishing-emails-utilize-azure-blob-storage/) to fool unsuspecting victims.
Using Azure blob storage for phishing does not only give attackers access to a legitimate-sounding domain (*.web.core.windows.net), but it also gives the attacker a valid SSL certificate. Combining the legitimate domain with a legitimate certificate sounds like a recipe for disaster.
Phishing websites usually present unsuspecting victims with fake login screens. The entered credentials are usually sent to a different web server (usually in the background), and the user is then directed to the actual website being spoofed. This redirection comforts the unsuspecting user who at this stage probably believes that the password was entered incorrectly.
The events just described can be observed in the screenshot below. The screenshot illustrates the actions taken after submitting a password to the phishing domain. The location of the credential storage facility has been masked since it is unclear if the owners of the website were victims or involved in this campaign.
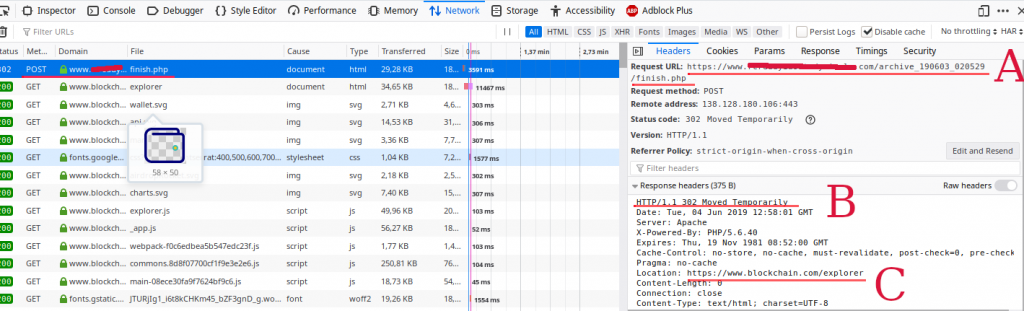
As can be seen, the credentials are first posted to a different server (A), then a redirect is performed (B) to the site being spoofed (C).
The following screenshot shows the website used by the attackers as a credential storage facility. Identifying characteristics have been masked. From the looks of things, the website was likely hacked.
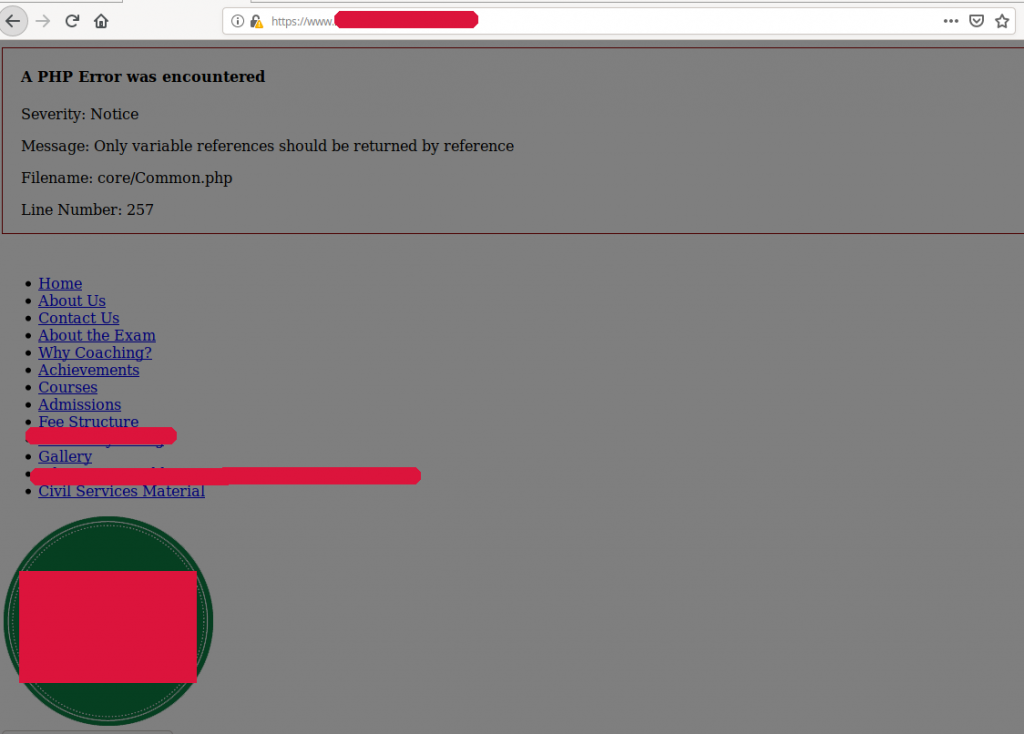
The attackers did not bother to configure the directory used to store their stolen credentials. It turns out that all credentials are logged to a file called “exploit.txt” by a script called auth.php script (the script that receives the actual credentials from the phishing site).
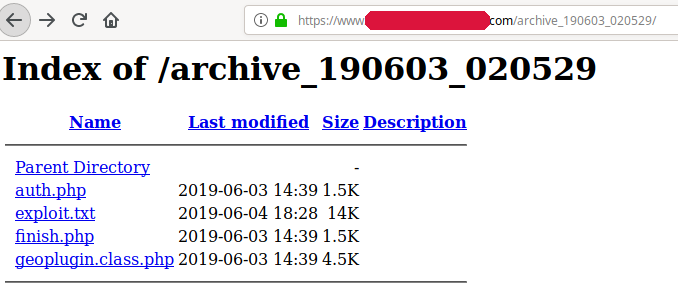
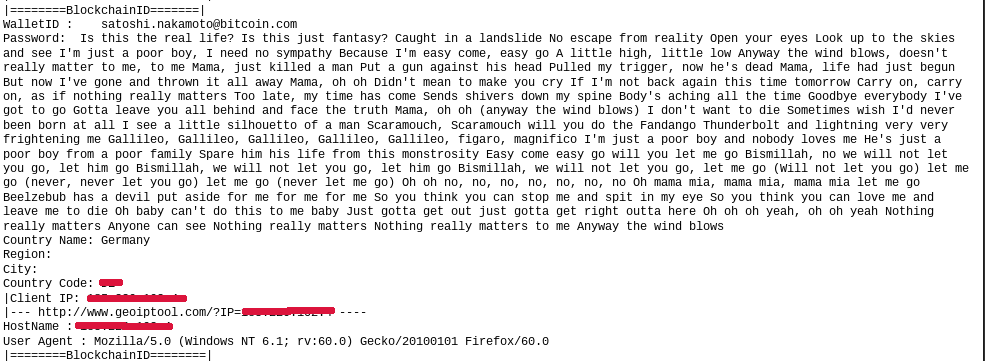
The credential database contains some necessary information about the person that submitted the credentials, including the wallet ID/email, password, IP and geographical location.
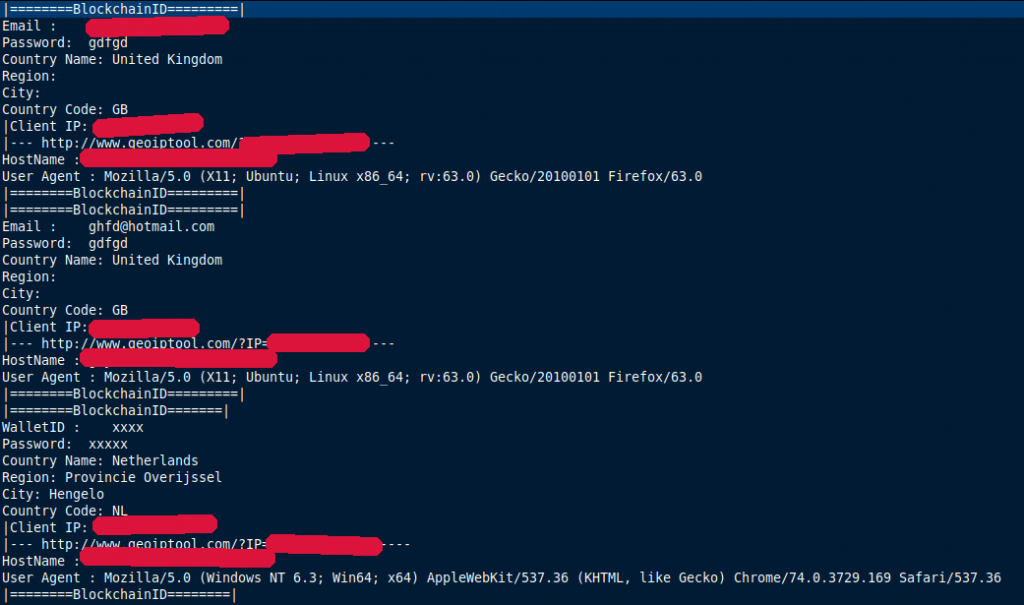
It turns out that most of the credentials found in the credential database are fake. The database contains both Bitcoin wallet IDs and email addresses with matching passwords. A total of 9 unique wallet IDs were observed, all of which were fake. The database also contained four email addresses of which one address seemed to contain a legitimate password.
- Wallet ID/Password: 9 entries with 0 legitimate entries.
- Email/Password: 4 entries with 1 entry that seems legitimate.
When considering that this phishing email was likely sent to thousands of email addresses around the world, it is very reassuring to know that only one email/password combination was found that seems to be legitimate. The legitimacy of the one account was not tested (due to ethical concerns).
As the title suggests, this is an article conveying a message of hope. The service provider hosting the website used by the phishers was identified, and an abuse report was submitted. Within a matter of hours, the service provider took down the phishing content (including the credential database).
The following message was received by the host after the take-down:
Unfortunately, things took

Just like the credential storage that was used before it was taken down, the new site also contained a file named “exploit.txt”. On this server directory listings were not allowed, which made it more challenging to locate the credential database. It was assumed that the attacker probably used the same scripts on the new server. This assumption turned out to be correct, and the credential database was also located on the new server.
This is where things got interesting: The previous database was destroyed in the take-down, which means that all entries in the database would effectively be fresh. The phishing campaign ran roughly a week on the new server before finally being killed – more on that later.
Withing that time 5 walled IDs were captured with zero legitimate passwords. Two email addresses were captured, also with zero valid passwords.
This is an extremely positive sign as it indicates that people are wising up to phishing attacks. The credential database contained numerous amu
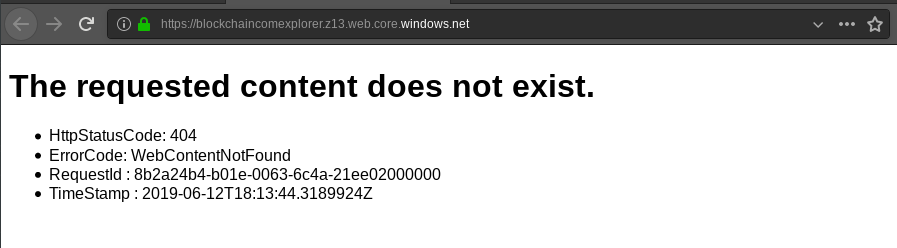
The original phishing site that ran at https://blockchaincomexplorer.z13.web.core.windows.net was reported to Microsoft. We waited a few days for the website to be taken down with no success. It turns out that Azure has a complaint facility designed especially for this purpose. After locating and using this facility, take-down occurred within a matter of hours.
After the take-down by Microsoft, the phishing site was not active anymore, as shown by the following screenshot.
It’s time-consuming to take down a phishing campaign. Everyone that has investigated phishing attempt would be able to attest to the resilience of phishers. Phishers are very resilient and taking down parts of an intricate phishing network may cause phishers to move their resources to other hosts.
The campaign investigated shows poor phishing success rates with only one seemingly valid credential captured. Considering that the phishing campaign organizers are taking a risk in running such a campaign, the only question that remains is if the reward is worth the risk.
The investigators at Crimson Wall have investigated many phishing campaigns with new ones emerging every week. Every now-and-then attackers manage to snag actual account details. Even if an attacker manages to capture only one valid account in 10,000 captured it can still be regarded as a success, because the cost of sending thousands of e-mails, hosting fees and other charges are marginal compared to the potential upside that can be produced by the occasional valid account captured.
When considering the costs, it can be argued that phishing attacks are not going to disappear anytime soon. Think about this before clicking on a link embedded in an e-mail.